Security is a major concern for any business or product, and with the increasing number of methodologies and toolkits to easily exploits the applications it becomes a more serious issue that needs to be focused on.
I liked the definition of "Vulnerability" from the Github's documentation:
A vulnerability is a problem in a project's code that could be exploited to damage the confidentiality, integrity, or availability of the project or other projects that use its code. Vulnerabilities vary in type, severity, and method of attack.
When your code depends on a package that has a security vulnerability, this vulnerable dependency can cause a range of problems for your project or the people who use it.
My observation as a developer is when we are developing an internal system or application for any client and if it's not a product we will rarely upgrade the dependencies because most of the time we upgrade those dependencies only to overcome any issue or bugfix.
Other than internal application or services, If we are working on any products we will keep on upgrading the third-party dependencies frequently but not all of them, only those that we are working on most and your application majorly depend on them, or in case there was a bug with the current version which got fixed in a newer version or some additional functionality is added to the library that will benefit the application.
However, what happens when the dependency is at risk, how would we get to know about such information? Will you keep a dedicated person to keep track of it 😝? or you will do it only when you get impacted by some serious exploit to your application? or you might have a static code analysis system in place which checks for any vulnerability in the code. However, what about the dependencies even in that case?
We need some kind of automated way to deal with this issue, and this is the exact issue that Github tried to solve and came up with this cool solution "Dependabot".
Dependabot will alert you whenever there is a vulnerable dependency found in your Github repository. Dependabot will refer the National Vulnerability Database, a combination of machine learning and human review to detect vulnerabilities in public commits on GitHub, Security advisories reported on GitHub, and FriendsOfPHP, and will use information from all these multiple sources to alert you.
As shown below, Dependabot works with a wide range of package managers & support languages that are widely used in the industry. Dependabot is still in beta, however, with future releases, you will see more of the tools support added to Dependabot.
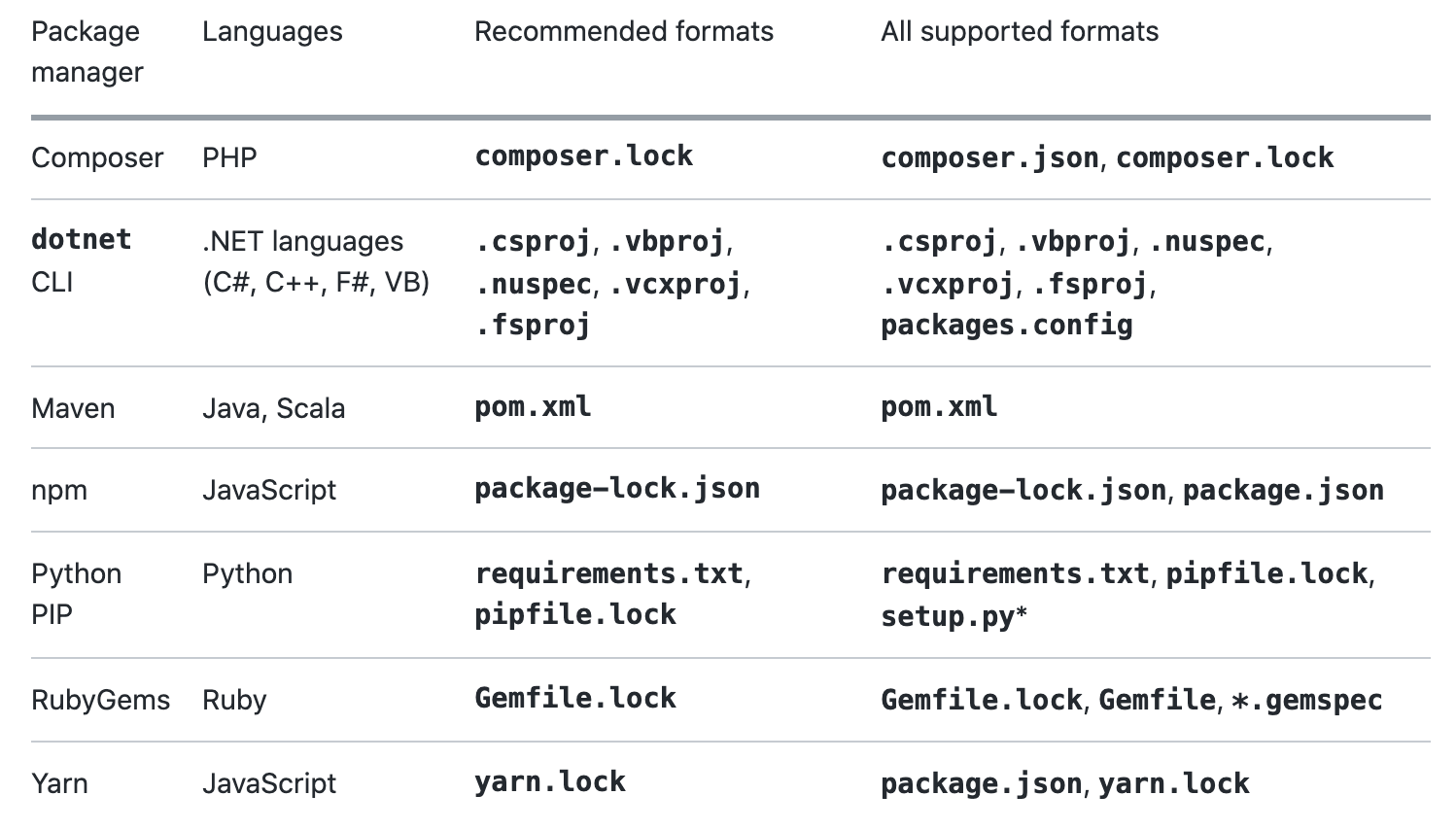
In this post, will see how to enable Dependabot in Github public repo, it's simple and has easy to configure steps.
Let's Go:
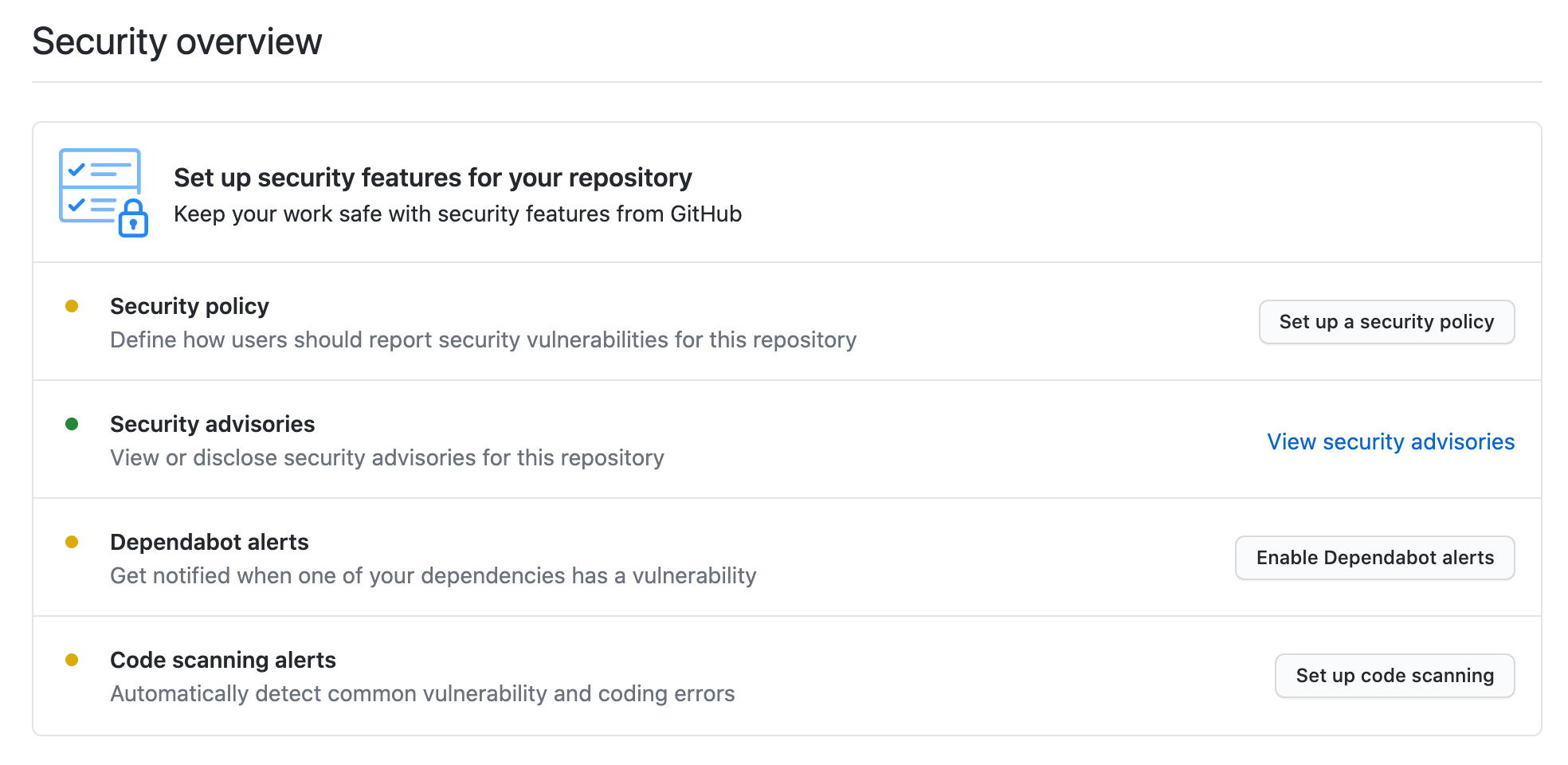
- Go to the security tab of the repository, and you will see the below screen, click on the
Enable Dependabot alerts.
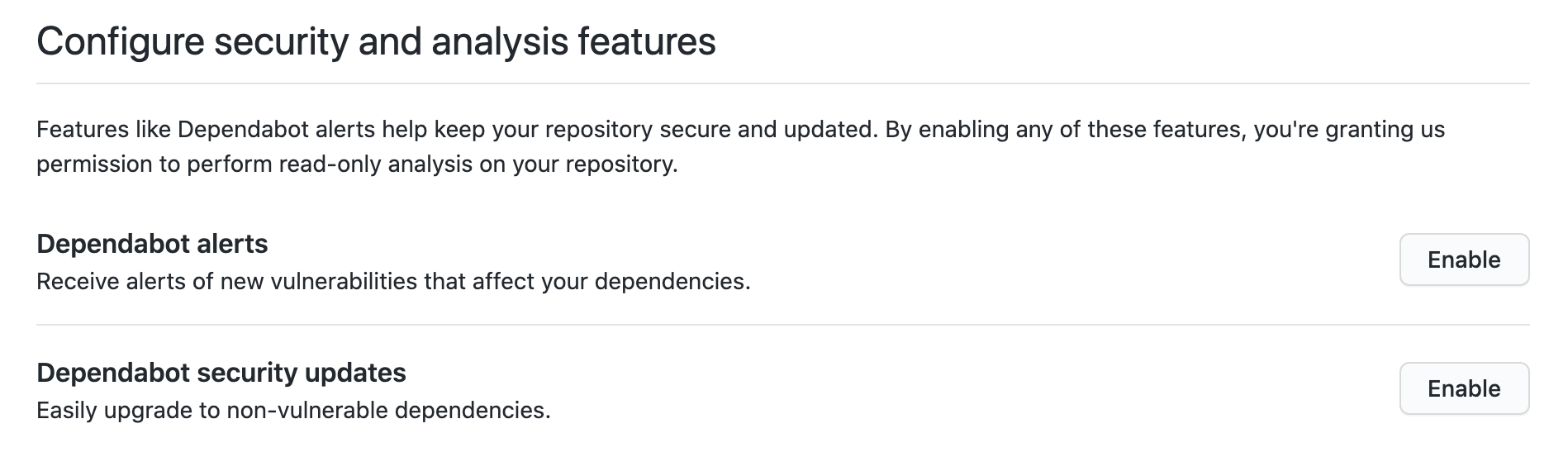
You will be shown the below screen which has two independent configurations, enable them based on your requirement.
- Dependabot alerts:
It will enable the dependabot to only show an alert on the main page when there's any vulnerability found in your repo. - Dependabot security update: [1]
It will raise a PR for upgrading any vulnerable dependencies to a safer version of those dependencies.
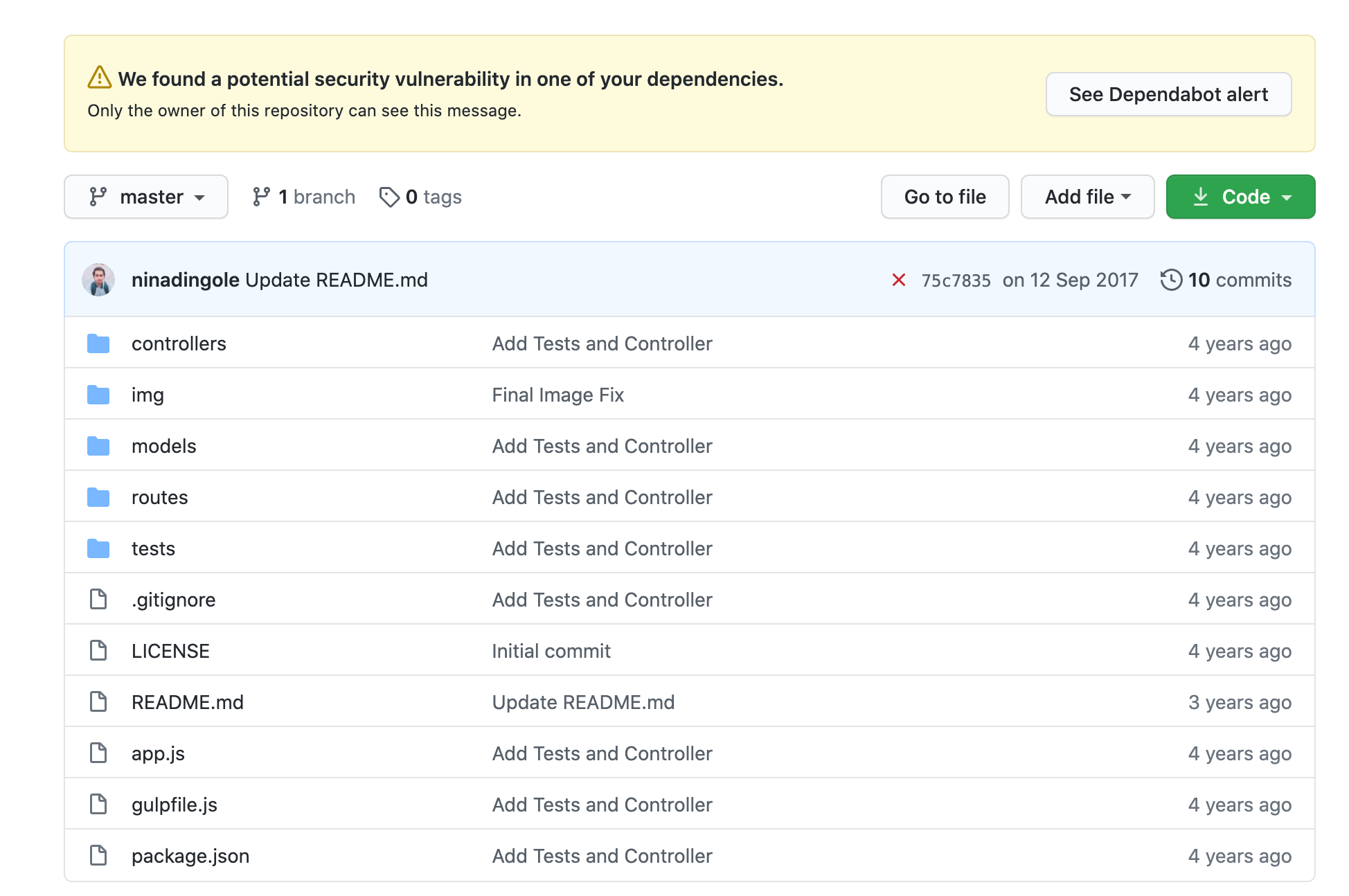
Once you enable the above options, it's all done. It's that easy to have this amazing functionality enabled for your repository.
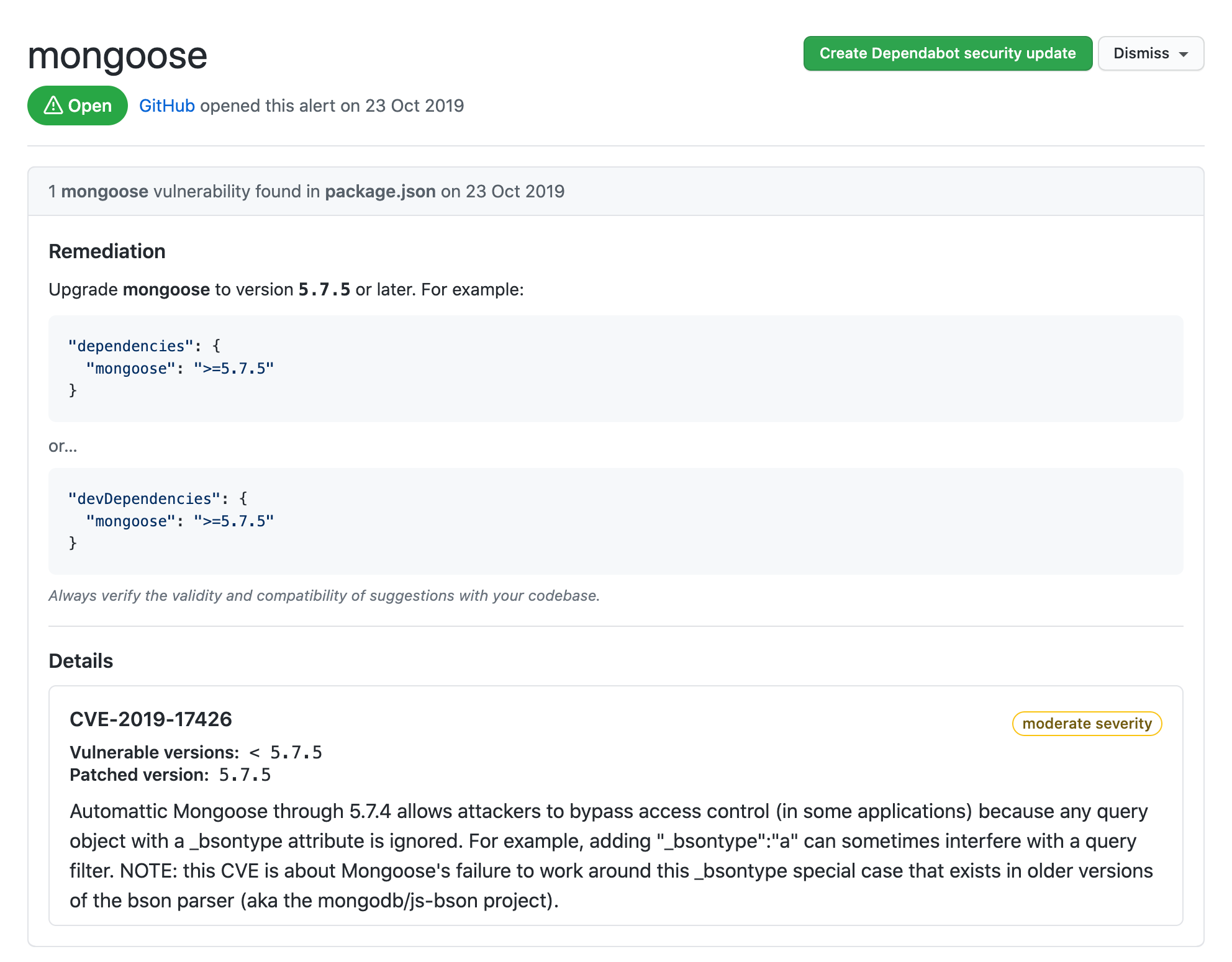
In the below screen you can see I got an alert for security risk in one of my repository in ExpressJS project.
On clicking See Dependabot alert, I found that the mongoose library that I am using is having a security issue with version 4.7.5. The details of the alert show me that the remediation is to upgrade the library to version >=5.7.5 and as my project is a NodeJS project it shows me how to do that in my package.json file.
Below is the remediation you can see the details of the security vulnerability, in this case, its allowing attackers to bypass access control 😝
How to fix this issue now? The details already show how to do it manually, but while enabling dependabot there's the second option that will automatically raise a PR for the version upgrade.
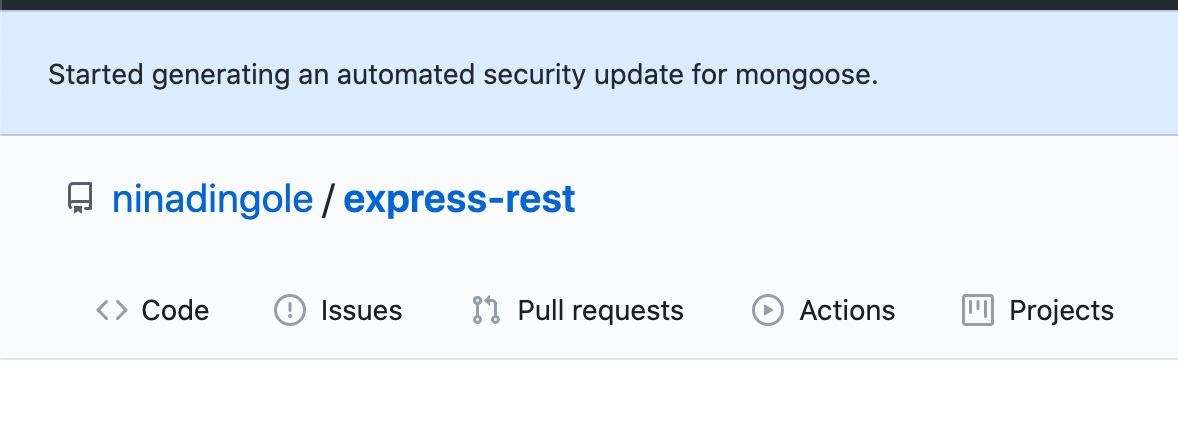
For this repository, I didn't enable the second option [1]. However, there's also another way. Click on Create Dependabot security update button in the above page, and it will start creating a PR for you, this is also a manual approach, and as you can see in the below image you will see a notification generated by the dependabot.
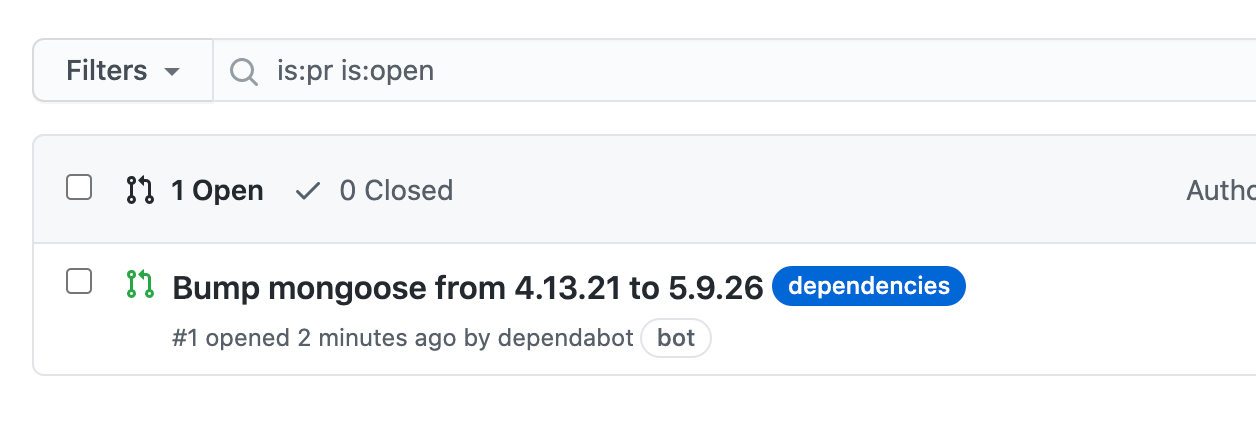
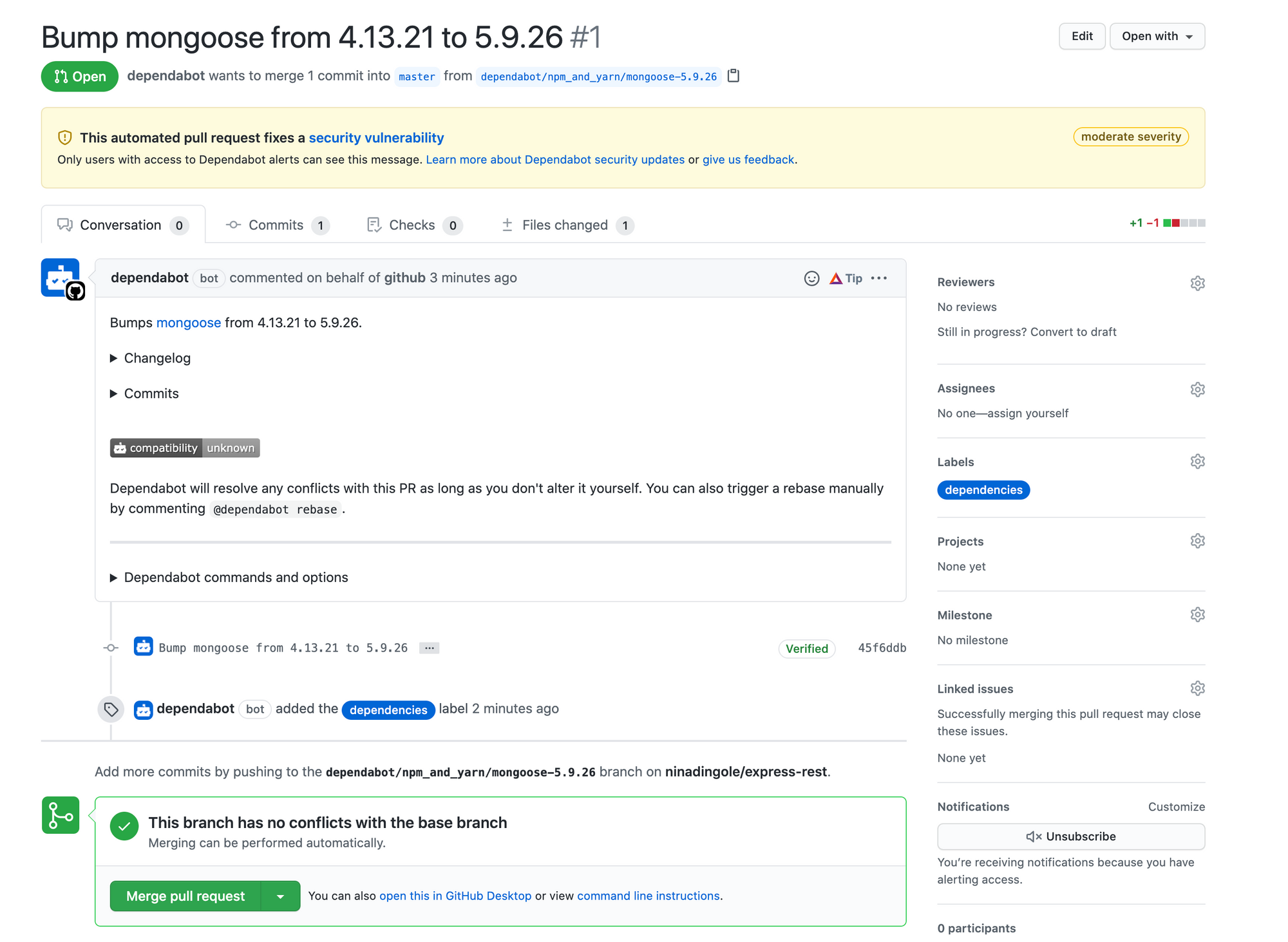
If you go to the Pull Request section of the repository you would see a Pull-Request being raised by the dependabot with tag dependencies I have seen similar PR's in a lot of open-source repositories.
And the same PR reference/link you will see in the security alert details now.
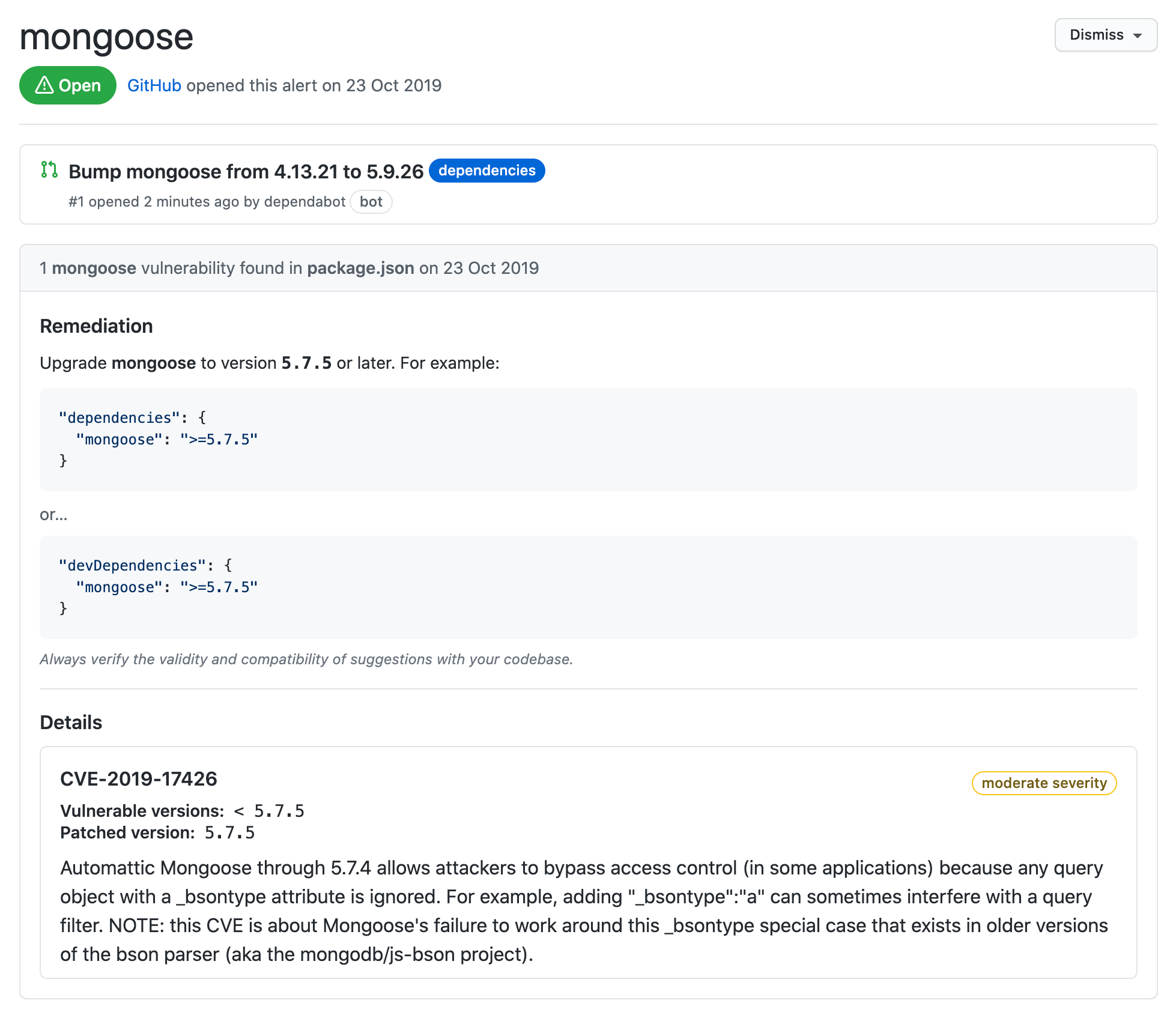
Further drilling down into the details of PR you could see more information about the PR, the PR upgrade the mongoose dependency to version 5.9.26 which is what was given in the remediation to upgrade to anything >=5.7.5. It also shows that the severity of this issue is moderate. Dependabot categories issue in four such categories you can read more about them here.
- Low
- Moderate
- High
- Critical
I didn't have any CI setup for this repository. However, if you have a test suite in the repository then this will also run all your test cases to see if this version works or not.
You can also see a Changelog for the recent changes to the library.
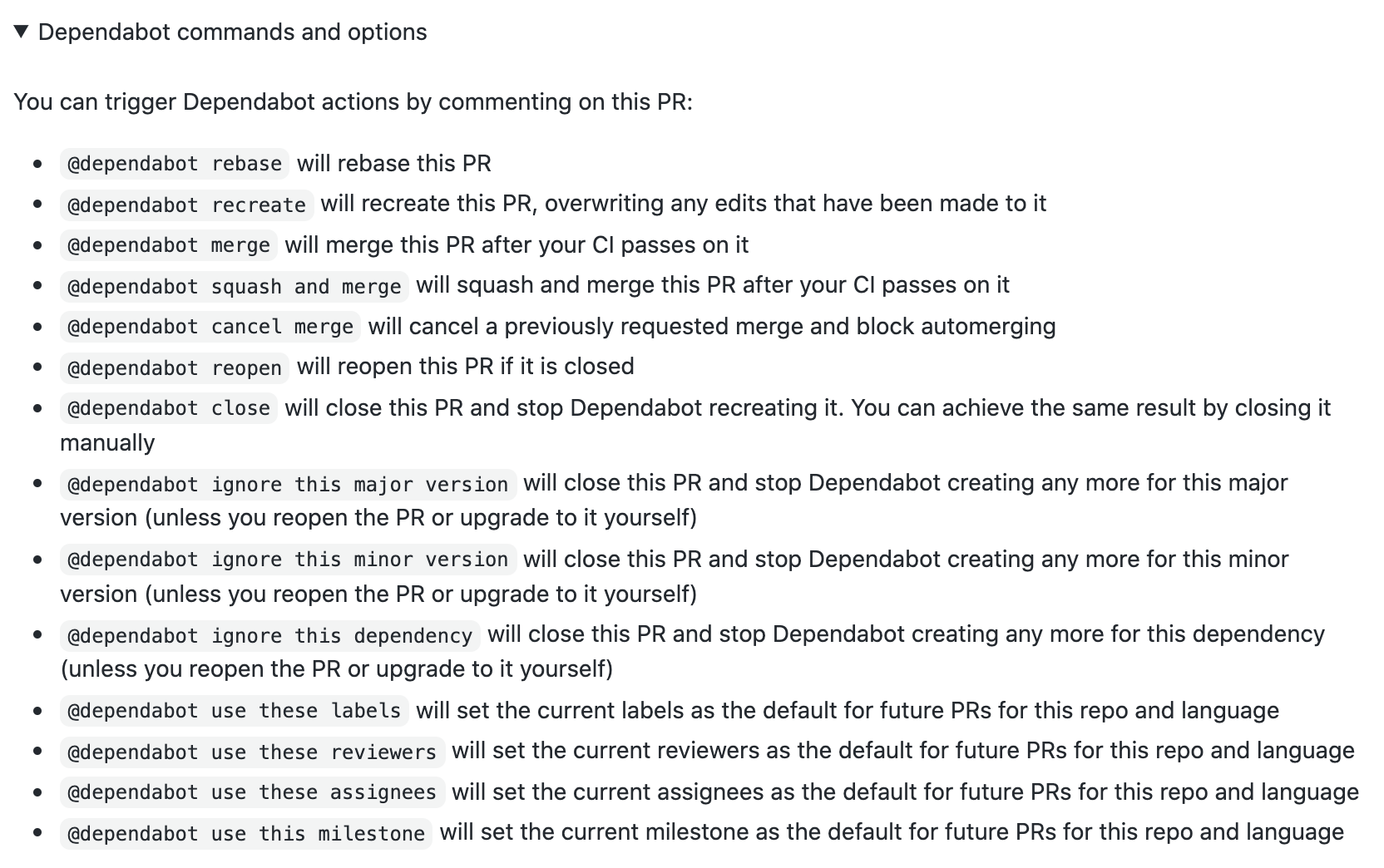
And there are some dependabot action commands as shown below that you can use in your comments to trigger actions like if you want to merge this PR instead of clicking on the merge button you can just comment in the PR @dependabot merge and this will merge the PR. You can squash, close, ignore and do all the below-given actions using comments.
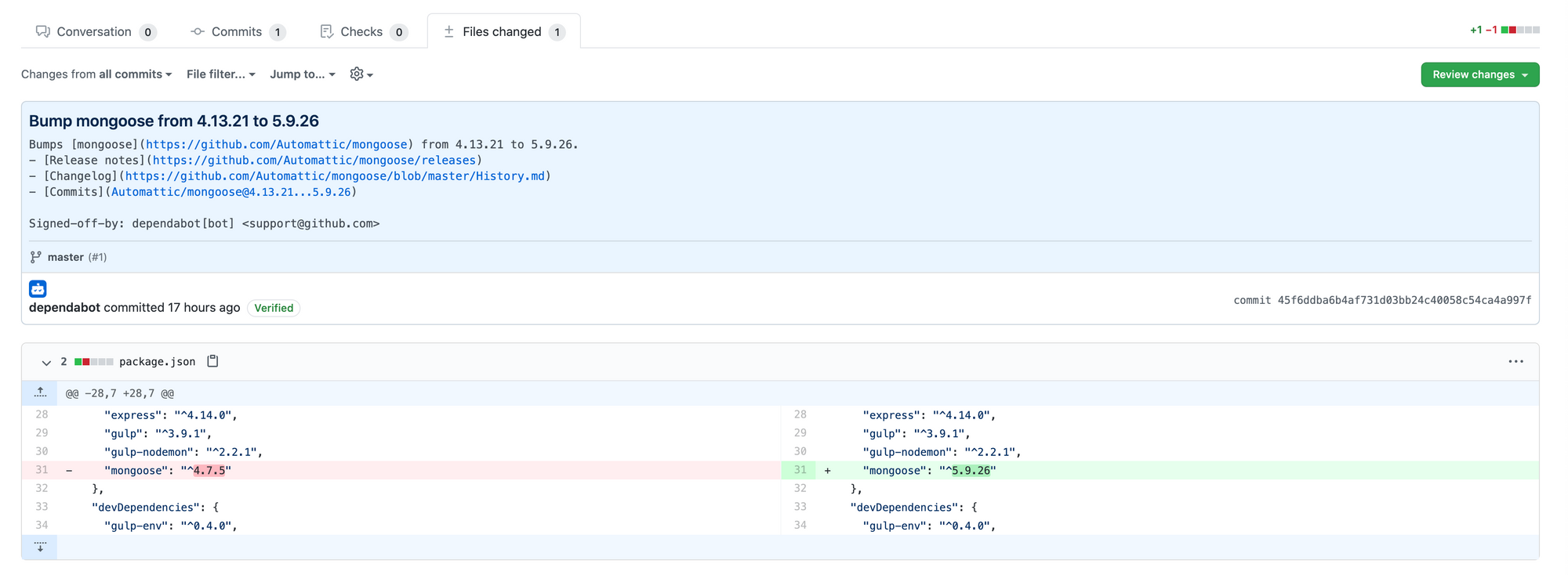
This is what the diff of the PR shows, the bot just updated a single line in my package.json file.
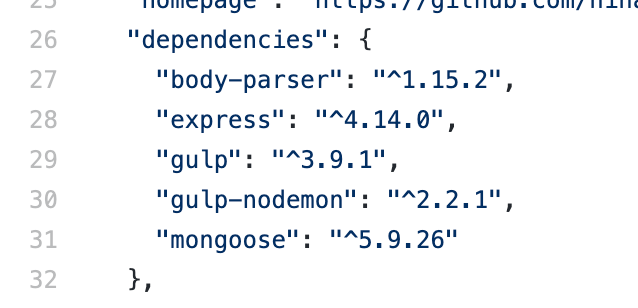
package.jsonOnce I merged the PR, this is the file content of my package.json 😀.
Wow, this will be the easiest thing to configure for the next project and comes with so many benefits. I hope this little blog post helps you to get rid of all those vulnerable dependencies in your project and keeps your business and application safe from some level of security threats. Make sure security is always a priority from the start of your project.
For any issues while following the steps or with the content do let me know down in the comments or email me using my contact page.
Don't forget to share the post with your friends & colleagues. Happy Coding!
